401 Authentication
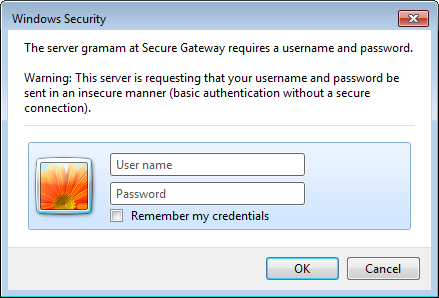
On Internet Explorer, it looks like this:
 On Chrome, it looks like this:
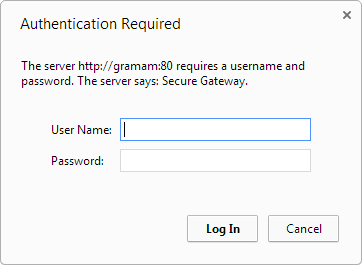
On Chrome, it looks like this:
 On Firefox, it looks like this:
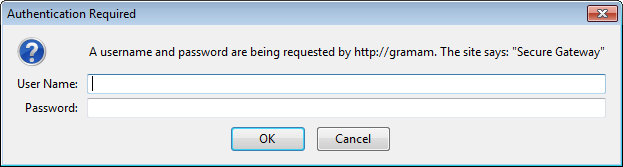
On Firefox, it looks like this:
 However, when navigated to the same site, Sahi automatically transforms this modal dialog into a simple web page.
However, when navigated to the same site, Sahi automatically transforms this modal dialog into a simple web page.
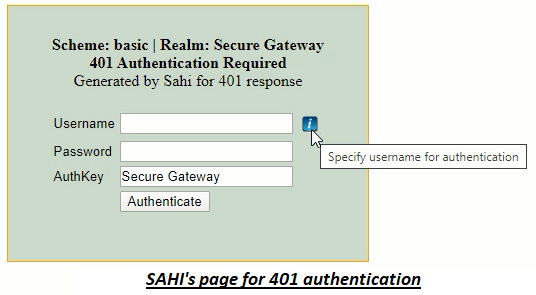 Since it is now just another HTML page, you can easily write scripts to enter username and password into the dialog.
Since it is now just another HTML page, you can easily write scripts to enter username and password into the dialog.
/Secure/ instead of Secure Gateway in the AuthKey field above.
To accept for any AuthKey one can use /.*/.
Try setting AuthKey to /.*/ before troubleshooting further.
To change the version of Java that Sahi Pro uses, edit
sahi/userdata/bin/setjava.bat (or setjava.sh)
and modify
set SAHI_JAVA_HOME=C:\path\to\java1.8401 authentication page for NTLM scheme loops or does not login even if the credentials are provided
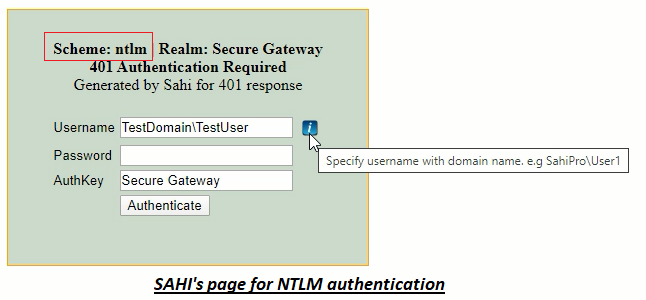
Sahi automatically tries to authenticate the WINDOWS logged in user for the applications which support NTLM scheme. However if Sahi is unable to authenticate the user automatically, the 401 page for NTLM authentication is displayed.
The solution would differ based on your environment. Thus to address this, employ below approaches one by one:
- First approach :
- Sahi automatically populates the username for the currently logged in user. However if you use different credentials for authentication, kindly enter them.
- Ensure that the username is in domain\user format where both the domain name and user name are correct.
- Provide your password for authentication in the password field and click on the Authenticate button.
- Second approach :
-
If the first approach did not work, then ensure that following property is enabled in the userdata.properties file :
apacheclient.enabled=true -
Add the following property in the userdata.properties file:
apacheclient.ntlm_authentication.enabled=true - Restart Sahi and then launch your application in the browser.
- Now enter valid credentials for authentication as done in the first approach.
Sahi authenticates automatically but the username is improper
Sahi automatically tries to authenticate the WINDOWS logged in user for the applications which support NTLM scheme. If successfully authenticated, Sahi's 401 authentication page will not be displayed. However you may wish to use different credentials i.e credentials of a user other than the currently logged in user.
To address this, follow below steps :
-
Add the following property in the userdata.properties file:
java.ntlm.transparent_authentication.enabled=false - Restart Sahi and launch your application.
- Now enter valid credentials for authentication. Ensure that the username is in domain\user format where both the domain name and user name are correct.
- Provide your password for authentication in the password field and click on the Authenticate button.
-
If it did not authenticate successfully, then ensure that following property is enabled in the userdata.properties file :
apacheclient.enabled=true -
Then add the following property in the userdata.properties file:
apacheclient.ntlm_authentication.enabled=true - Restart Sahi and try again.
Handling 401 authentication page for NEGOTIATE or KERBEROS scheme
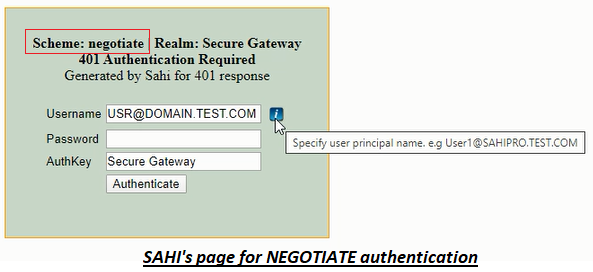
Sahi automatically tries to authenticate the user for applications which support only NEGOTIATE or KERBEROS scheme. However if Sahi is unable to authenticate the user automatically, the 401 page for authentication is displayed.
To address this, follow below steps :
-
Verify if
apacheclient.enabledproperty is set as true in the userdata.properties file. If this property is set as false, set it as true. Restart Sahi and try again. - If Sahi was unable to authenticate automatically even after enabling
apacheclient.enabledproperty, disable this property by setting it as false. Restart Sahi and try again. - Now Sahi's 401 page for authentication is displayed. Enter credentials in this web page.
-
Set User Principal Name as username in this web page. You can find your User Principal Name by running the command
whoami /upnon the command prompt. - Provide your system login password in the password field and click on Authenticate button. Restart Sahi and try again.
-
If the authentication did not succeed, ensure
apacheclient.enabledproperty is set as false. Then, set below properties in the userdata.properties file.- Run the command 'whoami /upn' on the command prompt. This command prints your User Principal Name. Set your User Principal Name as value for
java.kinit.principal_nameproperty. - Encode your system login password using Password Encoder. Set this encoded password as value for
java.kinit.encrypted_passwordproperty.
- Run the command 'whoami /upn' on the command prompt. This command prints your User Principal Name. Set your User Principal Name as value for
- Restart Sahi and try again. On start, Sahi will now generate a Kerberos ticket at
USER_HOME\krb5cc_USER_NAME. For example, if the Windows system's login user name isuserXYZ[icode], then the Kerberos ticket will be generated at [icode]C:\Windows\Users\userXYZ\krb5cc_userXYZ.
# Below example can be used to regenerate the ticket after every 500 minutes.
java.kinit.delay_between_regeneration=500401 dialog or page does not appear with Sahi
Sahi automatically tries to authenticate the WINDOWS logged in user for the applications. In this case, the 401 authentication page is not shown.
If Sahi is unable to authenticate the user automatically, the 401 authentication page should appear. If it does not appear, the application will not get authenticated access. Thus, the application will not behave as expected.
In such a case, where the application expects authentication but the authentication page does not appear, follow below steps.
- Ensure that
apacheclient.enabledproperty is set as true in the userdata.properties file. Also, verify ifjava.ntlm.transparent_authentication.enabledis set as true. After enabling these properties, restart Sahi and try again. - If Sahi's 401 page for authentication is displayed, enter credentials in this web page.
- If Sahi's 401 page for authentication is still not displayed, use API _setAuthentication to add credentials for authentication. Reload the application page.





