Restrict Remote Access to Sahi
Restrict Remote Access
Configure IP addresses to Restrict Remote Access
abstractSince Sahi Pro v9.0.0, now users are allowed to restrict remote access by adding the list of IP in whitelist and blacklist.
Sahi Pro now allows users to restrict remote access by adding the list of IP in allow and deny list.For allowing the access of any IP, user need to add list of IP in
sahi.xxx.remote_access.ip.allow
and for denying the access of any IP, user need to add list of IP in
sahi.xxx.remote_access.ip.deny.This feature is added since Sahi Pro v9.0.0.
info
Set the following property
For all these properties
sahi.remote_access.ip.restrictions.enabled to true in order to use below mentioned IP restrictions related properties.
Setting this to false will remove all below restrictions and allow access from any machine.
- Separate IPs with semi-colon.
- Wildcard * can be used for full ip address as well as each part(octet) of ip, * matches any sequence of number.
- square bracket can be used to match range for any part(octet) of IP.
e.g. 192.168.0.[0-255] matches any IP between 192.168.0.0 to 192.168.0.255 - PRIORITY: If same IP is entered in both "allow" and "deny" IP list, then priority will be given to "deny" IP list.
info
After doing any change in
Follow the below instructions to use these properties.
userdata_hidden.properties, user need to restart Sahi.
sahi.master.remote_access.ip.allowandsahi.master.remote_access.ip.deny- Master: IPs specified here can access and use this machine as a Master.
- Master role is responsible for triggering execution on itself and its Slave nodes.
- The IP of the Initiator, or Jenkins machine should be in the allow list.
sahi.slave.remote_access.ip.allowandsahi.slave.remote_access.ip.deny- Slave: IPs specified here can access and use this machine as a Slave node in distributed playback.
- The IP of the Master should be in the allow list.
sahi.configuration.remote_access.ip.allowandsahi.configuration.remote_access.ip.deny- Configuration: IPs specified here can change configurations of Sahi on this machine.
- The IP of Manager or Master should be in the allow list.
sahi.reports.remote_access.ip.allowandsahi.reports.remote_access.ip.deny- Reports: IPs specified here can access reports on this machine. This is needed on the machine which is configured as Central DB.
- IPs/IP ranges of machines of various business stake holders (developer, tester, manager etc.) can be added
- Reports profile does not impact on Reports syncing feature.
sahi.reports_sync.remote_access.ip.allowandsahi.reports_sync.remote_access.ip.deny- Reports Sync: IPs specified here can sync their reports to this machine.
- This is needed on the machine which is configured as Central DB.
- The IP of Master should be in the allow list.
sahi.mobile_execution.remote_access.ip.allowandsahi.mobile_execution.remote_access.ip.deny- Mobile Execution: IPs of Mobile Devices specified here can use this machine as their Sahi proxy.
- This is needed for Mobile Web automation on Mobile device.
sahi.remote_access.ip- Full Remote Access: This property will make all the Sahi features (master, slave, configuration, reports and mobile execution etc.) available to given IPs. This overrides all other settings for the specified IPs.
- Do not put the IPs here for which any/ some of the Sahi features needs to be denied.
//Examples to allow the access
//'*' remote master access is allowed for all IP address.
sahi.master.remote_access.ip.allow=*;
//'*' wildcard for last part (octet) of IP address is allowed for remote master access.
sahi.master.remote_access.ip.allow=192.168.1.*;
// remote master access is allowed only for 192.168.1.143.
sahi.master.remote_access.ip.allow=192.168.1.143;
// remote master access is allowed only for the range [0-255] of IP address.
sahi.master.remote_access.ip.allow=192.168.1.[0-255];
//Examples to deny the access
//'*' all the Sahi is restricted for remote master access.
sahi.master.remote_access.ip.deny=*;
//'*' wildcard for last part (octet) of IP address is restricted for remote master access.
sahi.master.remote_access.ip.deny=192.168.1.*;
// restriction for remote master access is only for 192.168.1.143.
sahi.master.remote_access.ip.deny=192.168.1.143;
// restriction for remote master access is only for the range [0-255] of IP address.
sahi.master.remote_access.ip.deny=192.168.1.[0-255];//Examples to allow the access
//'*' remote slave access is allowed for all IP address.
sahi.slave.remote_access.ip.allow=*;
//'*' wildcard for last part (octet) of IP address is allowed for remote slave access.
sahi.slave.remote_access.ip.allow=192.168.1.*;
// remote slave access is allowed only for 192.168.1.143.
sahi.slave.remote_access.ip.allow=192.168.1.143;
// remote slave access is allowed only for the range [0-255] of IP address.
sahi.slave.remote_access.ip.allow=192.168.1.[0-255];
//Examples to deny the access
//'*' all the Sahi is restricted for remote slave access.
sahi.slave.remote_access.ip.deny=*;
//'*' wildcard for last part (octet) of IP address is restricted for remote slave access.
sahi.slave.remote_access.ip.deny=192.168.1.*;
// restriction for remote slave access is only for 192.168.1.143.
sahi.slave.remote_access.ip.deny=192.168.1.143;
// restriction for remote slave access is only for the range [0-255] of IP address.
sahi.slave.remote_access.ip.deny=192.168.1.[0-255];//Examples to allow the access
//'*' remote configuration access is allowed for all IP address.
sahi.configuration.remote_access.ip.allow=*;
//'*' wildcard for last part (octet) of IP address is allowed for remote configuration access.
sahi.configuration.remote_access.ip.allow=192.168.1.*;
// remote configuration access is allowed only for 192.168.1.143.
sahi.configuration.remote_access.ip.allow=192.168.1.143;
// remote configuration access is allowed only for the range [0-255] of IP address.
sahi.configuration.remote_access.ip.allow=192.168.1.[0-255];
//Examples to deny the access
//'*' all the Sahi is restricted for remote configuration access.
sahi.configuration.remote_access.ip.deny=*;
//'*' wildcard for last part (octet) of IP address is restricted for remote configuration access.
sahi.configuration.remote_access.ip.deny=192.168.1.*;
// restriction for remote configuration access is only for 192.168.1.143.
sahi.configuration.remote_access.ip.deny=192.168.1.143;
// restriction for remote configuration access is only for the range [0-255] of IP address.
sahi.configuration.remote_access.ip.deny=192.168.1.[0-255];//Examples to allow the access
//'*' remote reports access is allowed for all IP address.
sahi.reports.remote_access.ip.allow=*;
//'*' wildcard for last part (octet) of IP address is allowed for remote reports access.
sahi.reports.remote_access.ip.allow=192.168.1.*;
// remote reports access is allowed only for 192.168.1.143.
sahi.reports.remote_access.ip.allow=192.168.1.143;
// remote reports access is allowed only for the range [0-255] of IP address.
sahi.reports.remote_access.ip.allow=192.168.1.[0-255];
//Examples to deny the access
//'*' all the Sahi is restricted for remote reports access.
sahi.reports.remote_access.ip.deny=*;
//'*' wildcard for last part (octet) of IP address is restricted for remote reports access.
sahi.reports.remote_access.ip.deny=192.168.1.*;
// restriction for remote reports access is only for 192.168.1.143.
sahi.reports.remote_access.ip.deny=192.168.1.143;
// restriction for remote reports access is only for the range [0-255] of IP address.
sahi.reports.remote_access.ip.deny=192.168.1.[0-255];//Examples to allow the access
//'*' All IP address can sync their reports to this machine.
sahi.reports_sync.remote_access.ip.allow=*;
//'*' wildcard for last part (octet) of IP address is allowed to sync their reports.
sahi.reports_sync.remote_access.ip.allow=192.168.1.*;
// Only 192.168.1.143 can sync its reports to this machine..
sahi.reports_sync.remote_access.ip.allow=192.168.1.143;
// All IPs address between 192.168.1.0 to 192.168.1.255 can sync their reports to this machine.
sahi.reports_sync.remote_access.ip.allow=192.168.1.[0-255];
//Examples to deny the access
//'*' No IP address can sync their reports to this machine.
sahi.reports_sync.remote_access.ip.deny=*;
//'*' wildcard for last part (octet) of IP address is restricted to sync their reports.
sahi.reports_sync.remote_access.ip.deny=192.168.1.*;
// 192.168.1.143 can not sync its reports to this machine.
sahi.reports_sync.remote_access.ip.deny=192.168.1.143;
// All IPs address between 192.168.1.0 to 192.168.1.255 can not sync their reports to this machine.
sahi.reports_sync.remote_access.ip.deny=192.168.1.[0-255];//Examples to allow the access
//'*' IPs of all Mobile Devices can use this machine as their Sahi proxy.
sahi.mobile_execution.remote_access.ip.allow=*;
//'*' wildcard for last part (octet) of IP address is allowed for remote proxy access.
sahi.mobile_execution.remote_access.ip.allow=192.168.1.*;
// remote proxy access is allowed only for 192.168.1.143.
sahi.mobile_execution.remote_access.ip.allow=192.168.1.143;
// remote proxy access is allowed only for the range [0-255] of IP address.
sahi.mobile_execution.remote_access.ip.allow=192.168.1.[0-255];
//Examples to deny the access
//'*' IPs of any Mobile Devices can not use this machine as their Sahi proxy.
sahi.mobile_execution.remote_access.ip.deny=*;
//'*' wildcard for last part (octet) of IP address is restricted for remote proxy access.
sahi.mobile_execution.remote_access.ip.deny=192.168.1.*;
// restriction for remote proxy access is only for 192.168.1.143.
sahi.mobile_execution.remote_access.ip.deny=192.168.1.143;
//restriction for remote proxy access is only for the range [0-255] of IP address.
sahi.mobile_execution.remote_access.ip.deny=192.168.1.[0-255];Configure login Restrict Remote Access
abstract
Any user on the network (if IP is allowed to access the resource) could access Sahi Pro via web browser and modify its configuration and settings.
This feature helps prevent other remote machines from directly accessing the Logs and Configuration of the host machine. Since Sahi Pro v6.2.0
To restrict remote machines from accessing Sahi Pro:
This feature helps prevent other remote machines from directly accessing the Logs and Configuration of the host machine. Since Sahi Pro v6.2.0
- Open Dashboard --> Configure --> Configure Users
- Check the checkbox "Enable Login"
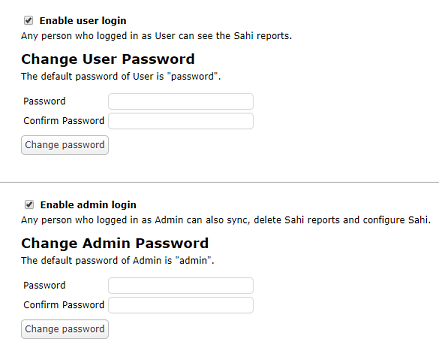
- Admin login can restrict configuring Sahi as well as to sync and delete Sahi reports.
- User login is the subset of Admin and can restrict the access to Sahi reports.
- The default password for user is "password" and for admin is "admin".
When users try to access restricted areas of Sahi Pro, they will be prompted with a login dialog.
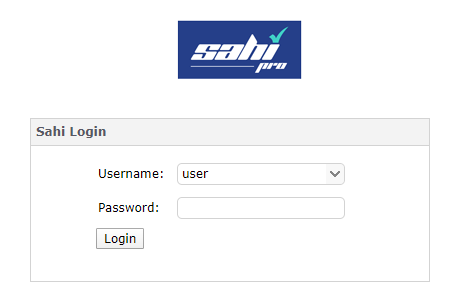
Allow Access to Restricted Sahi Pro
admin/password is the default User/password combination. User can change the password for admin.The remote machine has to login again if the host machine has restarted Sahi.





